Unicode: It is more than funny domain names.
When people discuss the security implications of Unicode, International Domain Names (IDNs) are often highlighted as a risk. However, while visible and often talked about, IDNs are probably not what you should really worry about when it comes to Unicode. There are several issues that impact application security beyond confusing domain names.
At first sight, Unicode is a standard that assigns numbers to characters [1]. It extends the ASCII standard, which only allowed for 127 different characters, to an essentially unlimited range of characters. With Unicode, we also have various encoding schemes, such as UTF-8 and UTF-16, that regulate how the respective code is expressed as a multi-byte value.
Unicode version 17.0 defines 159,801 different characters. This includes not only characters for various languages but also emojis and math symbols.
Here are some of the issues that are often overlooked:
Confusables
When discussing domain names, one issue that arises is the use of characters that are easily confused. The Unicode project has a tool to identify them [2]. But this issue goes beyond domain names. If you allow the full Unicode character set for usernames, users may be able to impersonate other users on your platform. This has frequently happened on X [3]. However, other platforms, such as internal messaging systems, could also be abused in similar ways.
Normalization and Best Fit Mapping
These techniques aim to address the issue that some systems are unable to represent the entire Unicode character range, but offer similar characters that can be used to represent these "missing" characters. The "confusable" tool mentioned above is also helpful to identify them. In its worst form, this could convert an otherwise harmless character, like a "FULLWIDTH GRAVE ACCENT", into a single quote, bypassing filters to prevent injection vulnerabilities. The key defense is to avoid any conversion after a string has passed input validation. However, unintentional conversion can happen on some platforms as data is inserted into databases.
Variant Selectors
"Variant Selectors" are non-printable ("invisible") Unicode code points that are used to specify an alternate representation of a given character. They may be used by first specifying a "normal" character, followed by a variant selector, and then an alternative character, such as an emoji. There are sixteen possible variant selectors. Selector-16 (#FE0F) would be used to define an emoji representation for a given character. Variant selectors were recently abused in the "Glass Worm" attack against VS Code extensions. In this case, variant selectors were used because they are not visible; they were used solely to encode obfuscated code snippets. The "Glass Worm" used sequences of variant selectors without following them up with an alternative glyph, which is not standard-compliant. Usually, each variant selector should be followed by a glyph.
Text Direction
Most languages are written/read left to right, and this is the default in most operating systems and editors. However, some languages use right-to-left. Unicode defines a "right-to-left (0x200F)" and "left-to-right (0x200E)" mark to indicate the direction. The direction may be changed at any point in the document. There are a few other Unicode code points that allow swapping the direction text is rendered (0x202A-E). Different text directions can be abused to make code reviews more difficult. A human reviewer will typically not see the change in direction, while a compiler or interpreter will, and as a result the code execution is different from what the human reviewer observed. There is a nice demo of this issue at trojansource.code [5]
[1] https://unicode.org/
[2] https://util.unicode.org/UnicodeJsps/confusables.jsp
[3] https://isc.sans.edu/diary/28440
[4] https://www.koi.ai/blog/glassworm-first-self-propagating-worm-using-invisible-code-hits-openvsx-marketplace
[5] https://trojansource.codes/
--
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
SmartApeSG campaign uses ClickFix page to push NetSupport RAT
Introduction
This diary describes a NetSupport RAT infection I generated in my lab from the SmartApeSG campaign that used a ClickFix-style fake CAPTCHA page.
Known as ZPHP or HANEYMANEY, SmartApeSG is a campaign reported as early as June 2024. When it started, this campaign used fake browser update pages. But it currently uses the ClickFix method of fake CAPTCHA-style "verify you are human" pages.
This campaign pushes malicious NetSupport RAT packages for its initial malware infection, and I've seen follow-up malware from these NetSupport RAT infections.
How To Find SmartApeSG Activity
I can usually find SmartApeSG indicators from the Monitor SG account on Mastodon. I use URLscan to pivot on those indicators, so I can find compromised websites that lead to the SmartApeSG script.
The Infection
Sites compromised through this campaign display pages with a hidden injected script. Given the right conditions, this script kicks off a SmartApeSG chain of events. The image below shows an example.
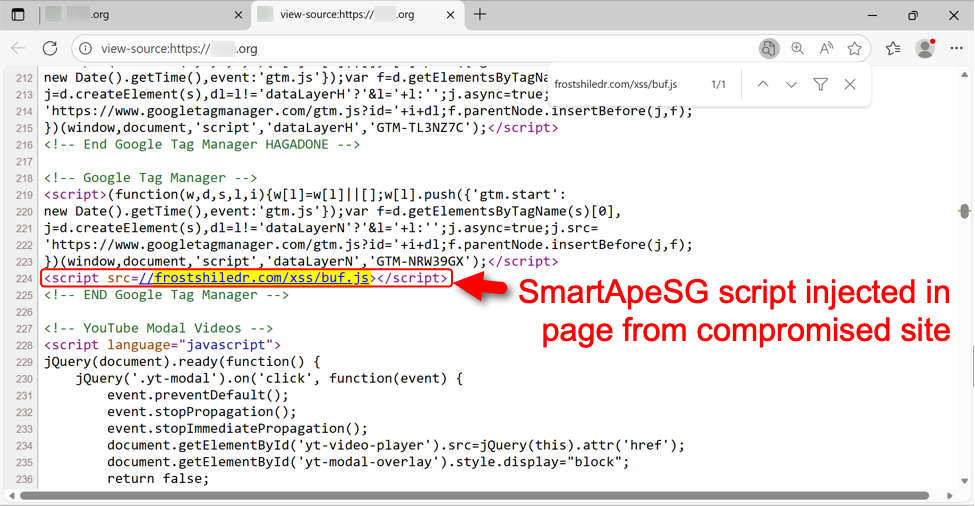
Shown above: Injected SmartApeSG script in a page from the compromised site.
In some cases, this injected script does not kick off the infection chain. I've had issues getting an infection chain during certain times of day, or if I try viewing the compromised website multiple times from the same source IP address. I don't know what the conditions are, but if those conditions are right, the compromised site shows a fake CAPTCHA-style "verify you are human" page.
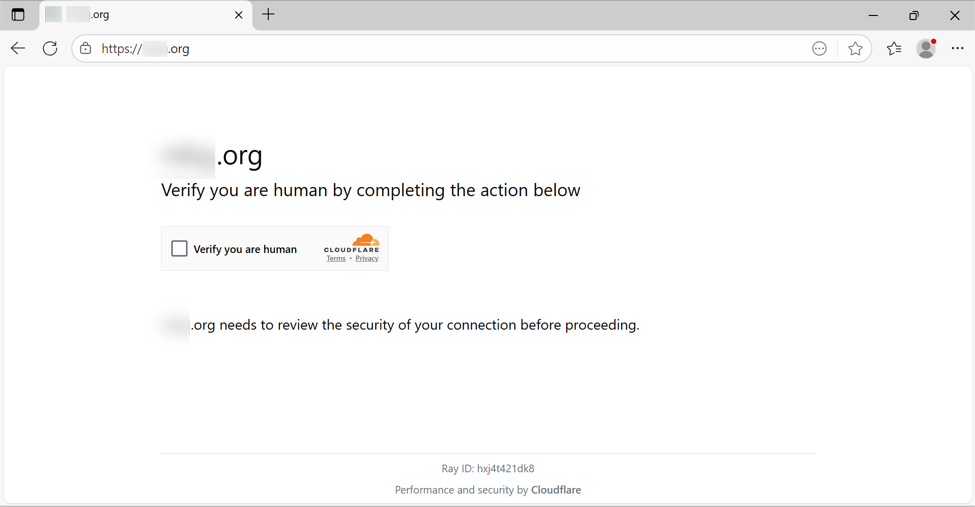
Shown above: Fake CAPTCHA page displayed by the compromised site.
Clicking the "verify you are human" box does the following:
- Injects malicious content into the Windows host's clipboard
- Generates a pop-up with instructions to open a Run window, paste content into the window, and run it.
The clipboard-injected content is a command string that uses the mshta command to retrieve and run malicious content that will generate a NetSupport RAT infection.
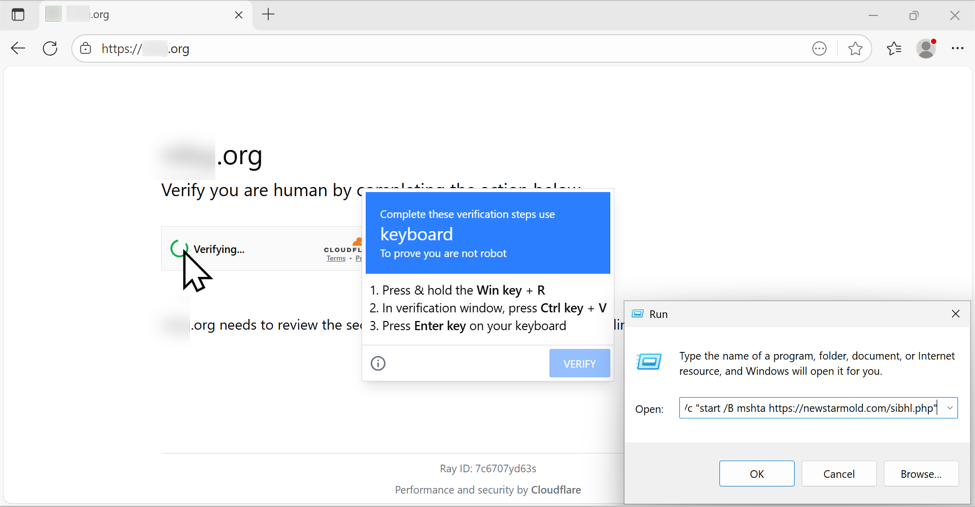
Shown above: Following ClickFix directions to paste content (a malicious command) into the Run window.
Below is a URL list of the HTTPS traffic directly involved in this infection.
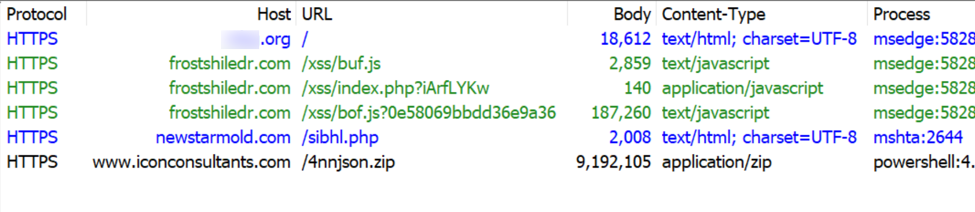
Shown above: HTTPS traffic directly involved in this SmartApe SG activity.
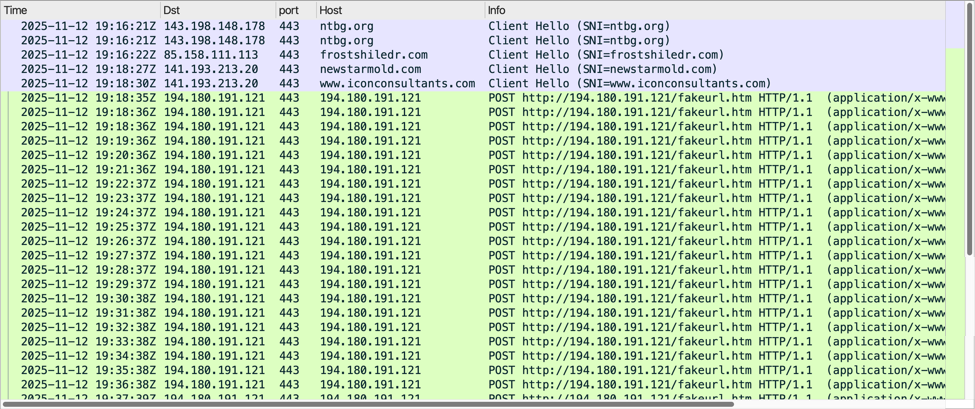
Shown above: Traffic from the infection filtered in Wireshark.
The malicious NetSupport RAT package stays persistent on the infected host through a Start Menu shortcut. The shortcut runs a .js file in the user's AppData\Local\Temp directory. That .js file runs the NetSupport RAT executable located in a folder under the C:\ProgramData\ directory.
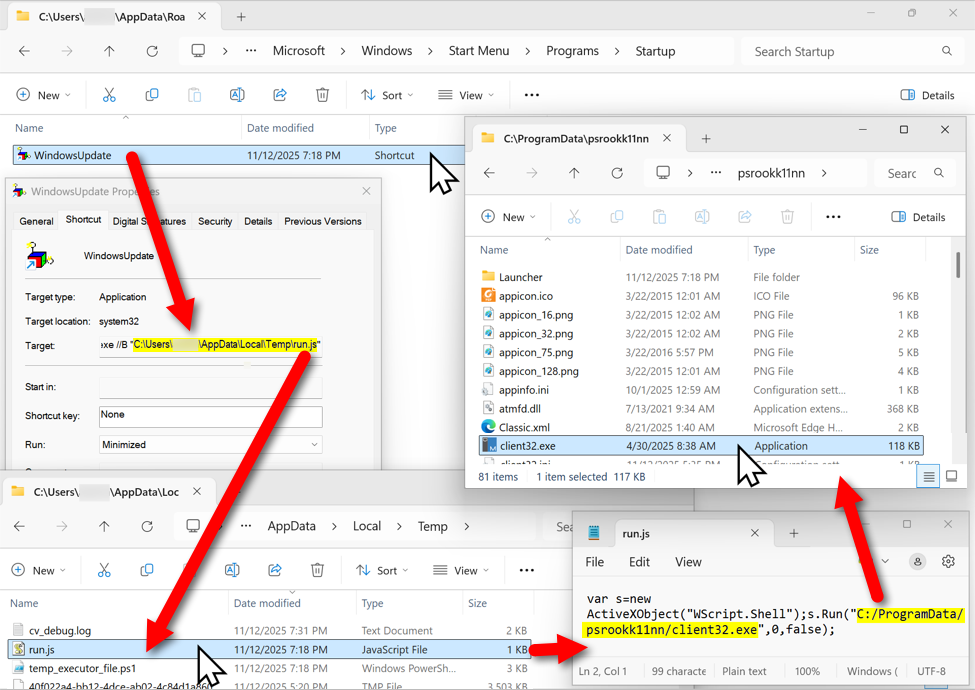
Shown above: The malicious NetSupport RAT package, persistent on an infected Windows host.
Indicators From This Activity
The following URLs were noted in traffic from this infection:
- hxxps[:]//frostshiledr[.]com/xss/buf.js <-- injected SmartApeSG script
- hxxps[:]//frostshiledr[.]com/xss/index.php?iArfLYKw
- hxxps[:]//frostshiledr[.]com/xss/bof.js?0e58069bbdd36e9a36 <-- fake CAPCHA page/ClickFix instructions
- hxxps[:]//newstarmold[.]com/sibhl.php <-- Script retrieved by ClickFix command
- hxxps[:]//www.iconconsultants[.]com/4nnjson.zip <-- zip archive containing malicious NetSupport RAT package
- hxxp[:]//194.180.191[.]121/fakeurl.htm <-- NetSupport RAT C2 traffic over TCP port 443
The following is the zip archive containing the malicious NetSupport RAT package:
- SHA256 hash: 1e9a1be5611927c22a8c934f0fdd716811e0c93256b4ee784fadd9daaf2459a1
- File size: 9,192,105 bytes
- File type: Zip archive data, at least v1.0 to extract, compression method=store
- File location: hxxps[:]//www.iconconsultants[.]com/4nnjson.zip
- Saved to disk as: C:\ProgramData\psrookk11nn.zip
Note: These domains change on a near-daily basis, and the NetSupport RAT package and C2 server also frequently change.
---
Bradley Duncan
brad [at] malware-traffic-analysis.net


Comments